After plowing the web for quite some time looking for a guide on how to set up certificates on a RDS-farm using an internal CA; I figured out a couple of things:
1) It’s actually pretty easy; but a bit tedious.
2) Apparently noone bothers making guides for easy things; and after writing this guide, I fully understand that.
Don’t be intimidated by the length of all of this, you only have to do it once, and it’s all GUI based.
First off: you’ll need an Enterprise CA in you domain. I haven’t tried this with a standalone CA, but I imagine it’ll be a bit trickier.
Installing the CA, if you haven’t done it, is pretty straight forward. Just two warnings first:
1) If at all possible, don’t install it on a DC. In my experience you might be in a world of frustration trying to figure out DCOM permissions and service privileges. You’ll probably be fine, but if you get into trouble, you’re pretty much on your own. There aren’t really that many people in the world with extensive knowledge of the intricate workings of a CA, and if you’re reading this, you’re not one of them.
2) Best practice is to put the database and log files for the CA on a separate drive (as with all such things), though depending on your environment, that may not be a must. But keep it in mind.
So: fire up the Server Manager, click Add Roles, and select Active Directory Certificate Services. Aside from moving the database, keep the default settings. You might need web enrollment for other things, but not this.
Reboot the server (do it even if not prompted for good measure), and your CA is up and running. Congrats!
Now you need to define an RDS template. Lord knows why this isn’t built-in; but I guess why that’s why he created consultants (such as myself).
The RDS team has this pretty much down to a tee on their blogpost, as they should, since they made the damn thing. I’ll paste the relevant section here; check out the blogpost for other details.
http://blogs.msdn.com/b/rds/archive/2010/04/09/configuring-remote-desktop-certificates.aspx
Creating Remote Desktop certificate template:
- On the computer that has your enterprise Certification Authority installed start MMC and open the “Certificate Templates” MMC snap-in.
- Find the “Computer” template, right-click on it, and then choose “Duplicate Template” from the menu.
- In the “Duplicate Template” dialog box, choose “Windows Server 2003 Enterprise” template version.
- The “Properties of New Template” dialog box will appear.
- On the “General” page of this dialog box, set both “Template display name” and “Template name” to “RemoteDesktopComputer”. Note: it is important to use the same string for both properties.
- On the “Extensions” page, select “Application Policies”, and then click the “Edit…” button.
- The “Edit Application Policies Extension” dialog box appears.
- Now you can either remove the “Client Authentication” policy leaving the “Server Authentication” policy, or you can use the special “Remote Desktop Authentication” policy. Doing the latter will prevent certificates based on this template from being used for any purpose other than Remote Desktop authentication.
- To create the “Remote Desktop Authentication” policy, first remove both the “Client Authentication” and “Server Authentication” policies, and then click “Add…”
- The “Add Application Policy” dialog box appears. In this dialog box click the “New…”
- The “New Application Policy” dialog box appears. In this dialog box, set “Name” to “Remote Desktop Authentication” and “Object Identifier” to “1.3.6.1.4.1.311.54.1.2”, and then click “OK.”
- Select “Remote Desktop Authentication” in the “Add Application Policy” dialog box, and then click “OK.”
- Now the “Edit Application Policies Extension” dialog box should look like this:
- Click “OK” in this dialog box, and then click “OK” in the “Properties of New Template” dialog box.
So after finishing the above steps; open the template again, and go to the ‘Subject name’ tab. And make sure it’s set to “supply in request”. This will enable you to specify names in the certificate as you please.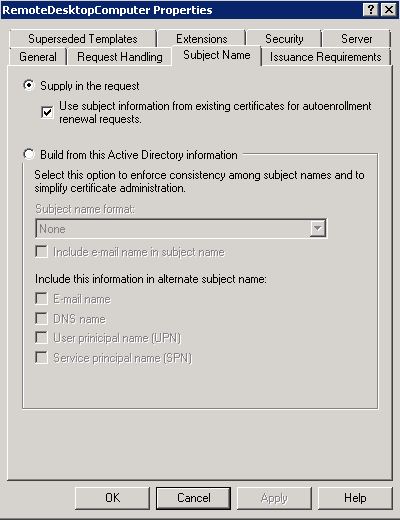
Click OK; and your template is ready.
The next step is to make the template you created available on your CA.
Open your Certification Authority management console – right click Certificate Templates, and select New – Certificate template to issue:
Select the Remote Desktop template and click OK.
Good; now the CA is ready.
If you don’t see the template in the list, it’s a replication issue. Either wait, or reboot the server, and the template will appear.
Now you’ll need to define an auto-enrollment policy. Quite simply this a GPO which will enable AD-integrated certificate enrollment.
I set this on the top level of the domain, but keep in mind that this will enable anyone in the domain to request a certificate. That’s not usually a problem, since you likely trust your own domain computers, but this should obviously comply with company policy. The configuration should be set under: User Configuration – Windows Settings – Public Key Policies.
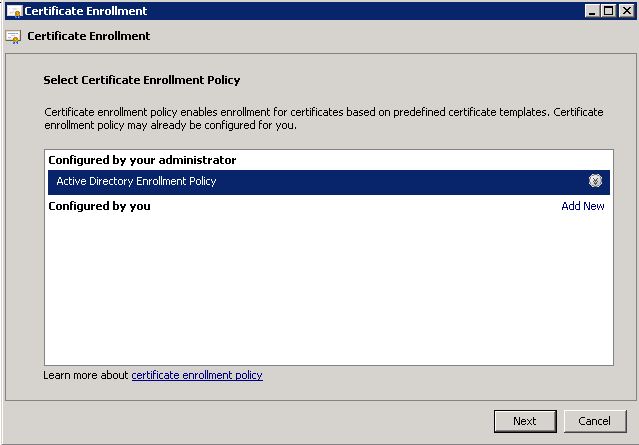
Open Certificate Services Client – Certficate Enrollment Policy. Enable this and click ‘add’.
Select ‘Use default….’ and click add. Now it should look like this:
Now, wait for the policy to replicate, or run a gpupdate; whatever floats your boat.
Keep in mind that after installing a CA; the root certificate of this CA will only replicate to clients/server during startup (correct me if I’m wrong here). So if you haven’t booted the RDS servers, you won’t get any options for auto-enrollment. If you’re not able to boot them, you can manually install the root sertificate by exporting it from the CA and importing it as a trusted root certification authority on the servers. I won’t cover that here.
On the server, open MMC, click file – add/remove snapin; select certificates and local computer. This is the certificate store on your computer.
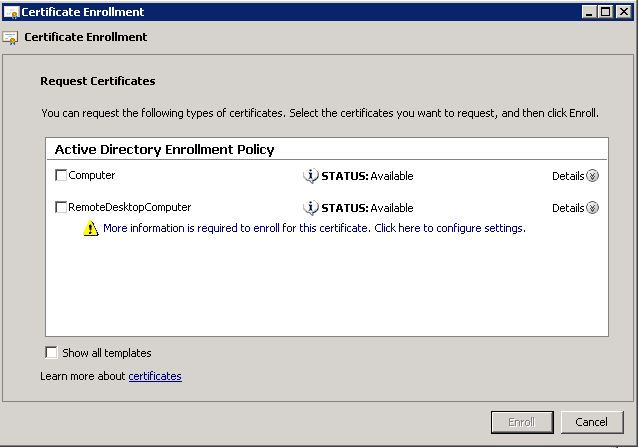
In order to request a new certificate, right-click ‘personal’ and select “All Tasks – Request New Certificate”. Click next on the following dialog box. And you auto-enrollment policy should appear.
Click Next; and you should get something like this:
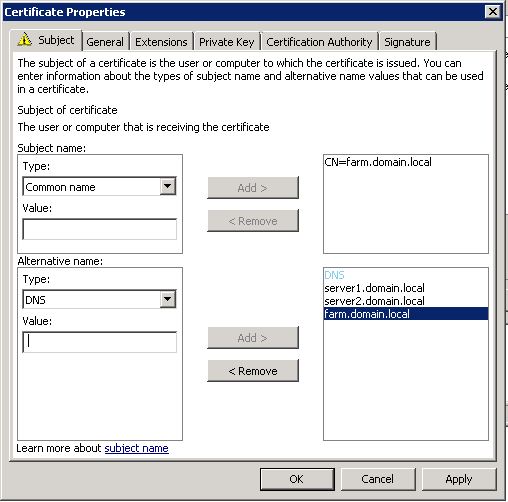
Select RemoteDesktopComputer, and click the ‘More information….’ link. This is because we’ve disabled using the AD computer account for identification, so that we can add the farm name.
In the following dialog-box, enter your farm-info:
Click ‘enroll’:
Success!!!
Now all that is left is to assign the certificate to the RDS-connection.
Go to Remote Desktop Host Configuration, and double-click the TCP connection.
On the ‘general’ tab; simply click Select at the bottom, and select your new certificate.
DONE!
Though you will need to do this on all farm servers; but not the broker.
And the clients also need to restart in order to get the CA Root certificate, which will authorize the new rds certificate.
Now go get a cup of coffee!








Great! thanks for the share!
ok this is great. But what about certificate for windows 7 client? does that need the same ” remote desktop certificate” its ok to configure for severs the subject name same as farm, but do windows 7 needs the same thing to be done manually to them? if there are 800 windows 7 computers, we cannot do it manually and how to solve the subject name for windows 7 clients? Also, in above, when you are adding the server farm name, are you adding the server name too?
when you are adding in alternative name type dns, what refers to server1 and server2 here? Are they dns servers in domain or are they rds servers? Please provide details
Clients don’t need certificates in order to connect. As long as you use an enterprise CA, they will trust the server certificate. Dns names should be for the farm, and each of the servers.
Does that help? 🙂
Pingback: Неудачное имя в ферме терминальных серверов « ILYA Sazonov: ITPro
Very nice article, helped a lot. Thanks!
And I was just woeidrnng about that too!
Thanks for the write up, cleared up quite a bit for me about RDS certificates and CA’s in general.
Great article!
One note: if you want users to be able to enter just “farm” in the RDC Connection server field on their workstation and not the full “farm.domain.local” just add “farm” as one of the DNS entries on the SAN cert in addition to the values shown above (farm.domain.local, server1.domain.local, and server2.domain.local).
Pingback: RDS Certificate Installation Steps in Server Farm - Share IT Skills
Great Article. It solved my problem. Thank you so much.
Could you maybe help with another problem, which occurred after this tutorial.
Now, all my clients try to request a RemoteDesktopServer Certificate.
I’m using the Group Policy in the Default Domain Policy: Computer Configuration -> windows Settings -> Public Key Policies -> Certificate Services Client – Auto-Enrollment:
Enroll new certificates, renew expired certificates, process pending certificate requests and remove revoked certificates Enabled
Update and manage certificates that use certificate templates from Active Directory Enabled
and: Automatic Certificate Request Settingsshow: Computer
and: Trusted Root Certification Authorities:
Allow users to select new root certification authorities (CAs) to trust: Enabled
Client computers can trust the following certificate stores: Third-Party Root Certification Authorities and Enterprise Root Certification Authorities
To perform certificate-based authentication of users and computers, CAs must meet the following criteria: Registered in Active Directory only
Any help is appreciated.
Thank you
Glad it helped 🙂
Now I haven’t seen that problem before. I’ll have a look at my setup. Essentially the problem is that they’re requesting the wrong type of certificate, right? You didn’t by any chance go wrong on step no 8 in creating the template?
“Now you can either remove the “Client Authentication” policy leaving the “Server Authentication” policy, or you can use the special “Remote Desktop Authentication” policy. Doing the latter will prevent certificates based on this template from being used for any purpose other than Remote Desktop authentication.”
If you don’t remove Client Authentication, this will probably be available to clients as well as servers.
Thanks. No, I didn’t go wrong. I guess, the problem is, that on our clients Remote Desktop is enabled, as well.
Do you have any further ideas? Change the security/permissions on the template maybe?
The error was in the linked msdn-Page, where they tell you to deploy the Template.
My mistake.
Thank you anyway.
Ah, cool. Glad you sorted it. There isn’t a whole lot of quality documentation on this unfortunately.
Hi great post!
Keep in mind that if you want to use the certificate also for signing RDP files (RemoteApp), the certificate template needs also the “Code Signing” template added as Application Policy.
Grtz
Hello, nice port, thanks a lot. But we have 15 TS Server in our Farm. Can i use this Certificate to export and import to all other 14 Server? What can i do if we need new TS Server in the Farm?
Thank you
Michael
Well, you would obviously need a new cert for each server; which is a bit of a hassle. I’ve usually gone over to Xenapp once the farm size goes beyond 3-4 server. Mainly because of the management benefits you get.
But if you want to go there, you would need a cert which includes the server name, and the farm name. One for each server. I’m afraid there’s no going around that, but it is pretty much a one-time thing, so it’s not too much work.
Thank you for the turorial! helped alot!
But im stuck on the last step. i install the cert on all rd servers but in session host config it do not show so i can select it.
Joakim: check the cert-addin to mmc (local computer) and see if the cert is there. If it is, there’s probably something wrong with the template assignment, so it isn’t recognized as a RDS-cert.
Great article – much easier to follow than the MS articles. On quick question – Ruuning Windows 2008 R2 – can the CA be installed on the STANDARD edition or do I still need the Enterprise (or Datacenter) edition to allow the use of the Certificate templates & enrollment options??
Hi, and thanks 🙂
For this, you can do it with Standard, that’s not a problem. Enterprise CA gives you some functionality, but nothing that’s needed for a regular PKI. I’ve needed enterprise for 802.1x authentication, but can’t think of anything else.
Though upgrading is a bit messy if you ever have to go there 😉
Glad to see an update of this site, after
forever.
I know this if off topic but I’m looking into starting
my own weblog and was curious what all is required to get setup?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very web smart so I’m not 100% positive. Any tips or advice would be
greatly appreciated. Appreciate it
Thank you so much!
Now it finally works!!!
Thanks a lot! I’ve spent probably two hours trying to do this. As you said, it is easy, but can be very frustrating.
I did everything you said but still get the certificate error. I viewed it and it shows the certificate issued to my local computer. I’m using an internal CA